Cybersecurity Consulting and Management
What People Say
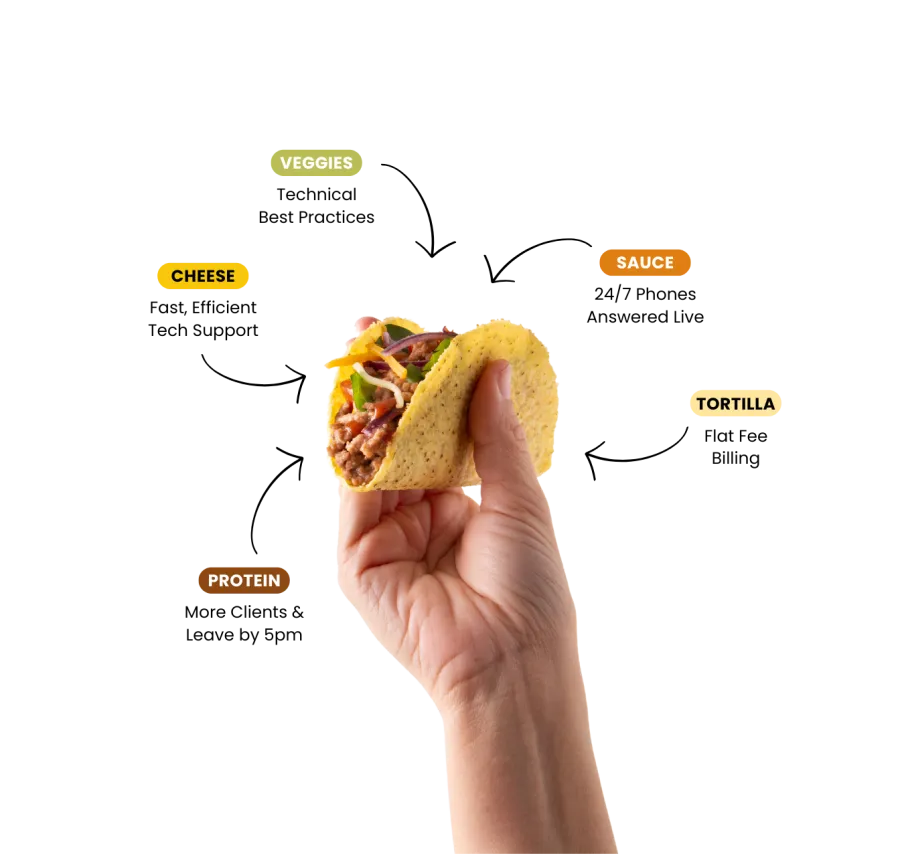
Our Tasty Taco Flavor Guarantee:
Satisfaction 90-Days In,
Or Your Money Back.
We're all in on your success. We'll outline goals together for our 90-Day mark, and if we don't hit them, you'll get your money back. Guaranteed.
Frequently Asked Questions
What is cybersecurity?
Why is cybersecurity important?
How can I protect my business from a data breach?
What is malware?
How can I protect my personal computer from malware?
This includes hardware, software, network configuration, and security, monitoring emails for spam-viruses, maintenance of computer systems, running diagnostics, and responding to network outages.
Our support specialists are trained to assess and understand your technology infrastructure, and your I.T. requirements.
They will recognize early warning signs of computer issues, other hardware or software failures, and act quickly to reduce the risk of downtime.
What is ransomware?
Our support services often result in businesses seeing an improvement in business operations, and the tools and strategies to move the business forward.



